November 8, 2022 Update: If you are interested in running Hyper-V within Hyper-V (rather than Hyper-V within VMware), please skip to the end of this Insights article.
Arsenal Image Mounter’s (AIM’s) ability to reliably and powerfully launch disk images into virtual machines has become one of its most popular features. While we recommend that Hyper-V and AIM be run on “bare metal” (particularly when launching virtual machines), we have recently heard from our customers that they have successfully run both Hyper-V and AIM within VMware.
Why would a digital forensics practitioner want to run Hyper-V and AIM within VMware? We are currently aware of two scenarios – Linux-only environments (where the use of Windows is not authorized on bare metal), and strict organizational policy regarding VMware usage.
We have found announcements from Microsoft and VMware about interoperability interesting, but we were skeptical about how well Hyper-V would really run within VMware. Once Kevin Ripa from SANS told us he was running Hyper-V and AIM within VMware, and successfully launching virtual machines from disk images, we started to become believers… with the caveat that if circumstances allow, we still recommend running Hyper-V and AIM on bare metal.
So, how do you make this work? Fortunately it’s quite easy and involves two significant steps:
1. Add the following three lines to your VMware virtual machine’s .vmx file (do not duplicate any of them if they already exist):
hypervisor.cpuid-ve="FALSE"
mce.enable="TRUE"
xhy…enable ="TRUE"
2. In your VMware virtual machine’s Processors settings, enable:
Virtualize Intel VT-x/EPT or AMD-V/RVI
Virtualize CPU performance counters
In our testing, once we took care of these two steps we were able to boot Windows, install and run Hyper-V, and run AIM just as if (performance aside) we were on bare metal.
If for some reason you are already running Hyper-V on bare metal, but you then want to run Hyper-V and AIM within VMware, things are a bit more complicated. These are the errors you will see if you try launching a VMware virtual machine, while Hyper-V is already running, using the settings we have given you in this article:
You might think that simply turning Hyper-V off from the “Turn Windows features on or off” options may be all you need to do, but you would probably be mistaken:
Windows virtualization-based security (VBS) uses Hyper-V, so (counter-intuitively) it is still running even if you have turned Hyper-V off in the “Turn Windows features on or off” options. You can verify this based on the output of msinfo32 (see the screenshot above) and by running “bcdedit /enum {current}” from an administrative command prompt:
To really stop Hyper-V from running, run “bcdedit /set hypervisorlaunchtype off” from an administrative command prompt:
After a reboot, you can confirm that Hyper-V is really off by running msinfo32 again:
Please take note that we are not fans of disabling Windows VBS, so (in addition to performance concerns) that is a compelling reason to run Hyper-V and AIM on bare metal when possible. Our testing related to this article was based on Windows 10, so once we were done we re-enabled VBS by running “bcdedit /set hypervisorlaunchtype auto” from an administrative command prompt. If you are beginning your virtual machine inception on Linux as opposed to Windows, this will not concern you.
Our testing related to this article was based on Windows 10 v20H2, VMware Workstation Pro v16.1.0 build 17198959, and Arsenal Image Mounter v3.3.136.
If you ever have the need to run Hyper-V and AIM within VMware, we hope you find this Insights article useful!
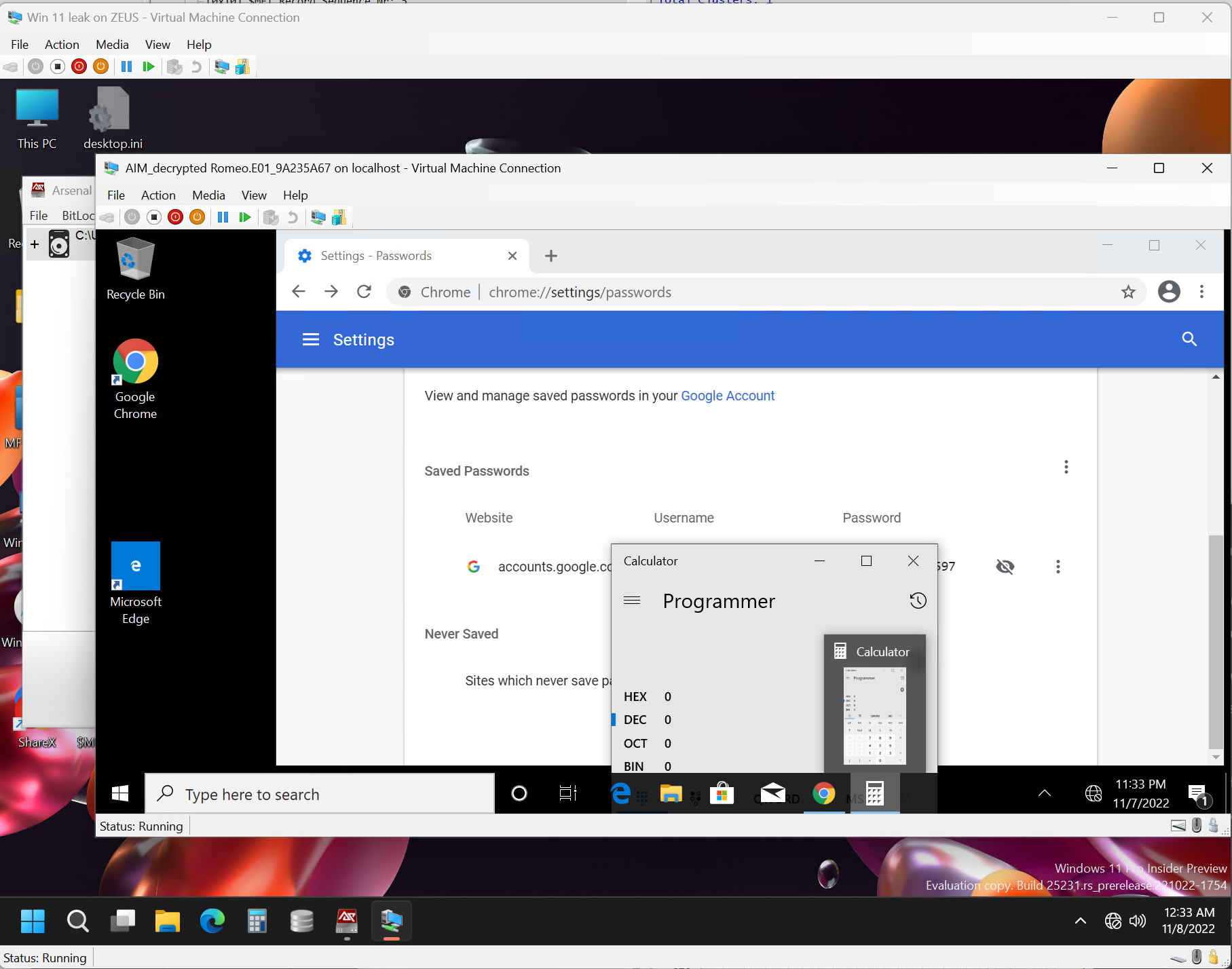
November 8, 2022 Update: Thanks to a recent question from Kevin Ripa and great response from Costas Katsavounidis, we are quickly covering how to run Hyper-V within Hyper-V in this article.
The key to successfully running Hyper-V within Hyper-V is enabling Hyper-V's nested virtualization on your host:
"Set-VMProcessor -VMName <VMName> -ExposeVirtualizationExtensions $true"
So the command recently run by Costas to launch Hyper-V on his forensic workstation was:
"Set-VMProcessor -VMName "Win 11 leak" -ExposeVirtualizationExtensions $true"
He was then able to run Arsenal Image Mounter within that Hyper-V running on his forensic workstation (named "Win 11 leak on ZEUS" in the screenshot below) to launch a VM (named "AIMdecrypted Romeo.E019A235A67") from a disk image - effectively running Hyper-V within Hyper-V: